We’ve all seen them and wondered. Every gadget suppler has a small electric fridge or cool-box, usually supplied with a cable to run it off a 12V vehicle supply. I’ve even seen some very favourable reviews of these devices, from people with no credentials. Then, last week I needed to cool down various perishable foodstuffs whilst on a road trip, so I bought one. This is a review of this particular unit, but the principles will apply to the whole family of products.
I opted for the Halfords 8-litre cool-box, largely because I knew where to find a Halfords and I knew I’d seen cool-boxes there. I chose the 8L version because I knew the cooling principle they all utilise isn’t very energy efficient; I didn’t want to cool more space than I needed.
The Halfords 8L cool-box is certainly well-made and insulated. It’s very solid, with a hinged lid and catch that suggests quality. This is only to be expected; the Halfords models are not cheap.

One nice feature of the 8L box is a fitting to hold it securely between two rear seats of a car using the lap belt, allowing it to double as an arm-rest. It’s also small enough to tuck away easily on one side of a boot. After fitting the supplied strap it’s also easy to carry and in another thoughtful touch there’s even a small compartment to store the power cable.
The power lead itself is long enough to reach from the dashboard to the boot without too much trouble and is fitted with a standard lighter plug on one end. The cool-box end of the lead has a proprietary connecting plug fitted, which might be tricky if a replacement is needed. Halfords do sell spare leads, but they’re not cheap!

Halfords also sells a mains adapter for something like £25 – ouch! This is one of the most expensive 12V adapters I’ve seen, but the cool-box is rated at 3A so you do need something a bit chunky. I decided against this purchase.
So far so good – the food was loaded into the cool-box and off we went with the cooler running while the engine was on. 3A is no problem for a car’s alternator but I didn’t want to drain the battery. The instructions also made it clear that running of the battery alone wasn’t a good idea.
However, at the end of the day’s driving, which amounted to several hours, it wasn’t at all clear that the inside of the box was any cooler than the outside. On our return I decided to test it properly to see what was going on.
Theory
These coolers all work using a thermoelectric effect. If you really want to know /how/ this works try looking up the Peltier or Seebeck effects in a good physics textbook. The short story is that if you take two plates made of different metals and place them together you can make a heat pump. As heat passes from the hot plate to the cold plate it generates a potential difference (voltage) between them. This is one of those electrical effects that works both ways, so if the plates are the same temperature and you pass a current across the plates they’ll drag heat from one plate to the other. In other words, is you pass a current through the two plates one gets hot by taking heat from the other, which gets cold.
This sounds very useful! All you need to do is place the plate that’s getting cold inside the box, and cool the plate that’s outside the box with a fan. This gives you a fridge with no moving parts apart from a fan, and as moving parts go, fan’s are a lot easier to manage than compressors and the associated plumbing for the coolant. Unfortunately there’s a snag – it’s not a particularly efficient process. Just how efficient it was in practice, I decided to find out.
Testing
Using a lab power supply and a several thermometers with remote probes to measure temperatures inside and outside the box I left the subject running while empty, after sealing down the lid. The inside and outside temperatures were recorded, with the inside being measured by the temperature of the plate.

The manufactures claim that it can reduce the temperature of the contents by up to 20C compared to the outside. With the normal summer temperature tending to be 20-25C and a reasonable fridge temperature being 5-10C this would certainly be a suitable performance even allowing for a margin implied by the ‘up to’ preceding the actual figure stated.
The actual performance is shown in Graph 1. As you can see, after about an hour the temperature inside dropped from the ambient 22C outside to just 3C inside, where it stabilised; a drop of 19C. Pretty impressive! But remember the 3A current drain – it turns out it needs 3A constantly so you definitely can’t run this without taking power off the engine. Sill, once cooled it should stay cool for a reasonable period, right? Actually, wrong. Take a look at Graph 2.
After disconnecting the power it returned to room temperature in about 20 minutes. Very disappointing!
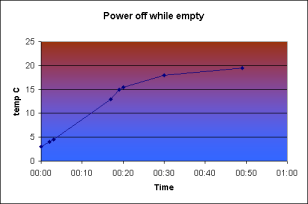
However, this isn’t really a good test, is it? Who needs to cool down a empty box – you really need to cool the contents, and what matters is how long the contents then stay cool once the power is removed. To test this I chose to use 1.5L of water in a sealed plastic box as the payload.

This choice was largely governed by the sealed plastic boxes I had available. There wasn’t space for 2L of water, so 1.5L was a compromise to make calculations easer – and besides, 1.5L or 1.5Kg of food is a reasonable payload for an 8L box. The results can be seen in Graph 3 below.

As you can see, after a full hour the temperature had only fallen by 3C – not much good to anyone. I decided to keep the experiment running for a further eight hours, during which the payload’s temperature eventually stabilised at 10C below ambient. The graph shows the measured temperature a bit lower, but by this stage the outside temperature had also dropped, so it was 10C less.
This isn’t really much good for cooling food down; even after running it all day it’s unable to reach ‘refrigerator’ temperature; your food wouldn’t last long. The only useful thing you can do with it is put pre-cooled items in it and hope they stay that way due to the insulation, because even with the power full on it’s only going to stabilise at about 10C . Graph 4 shows what happened.

As you can see, thanks to the insulation of the box it does at least manage to keep its contents cool. The tests were carried out away from the wind and sun – ideal conditions, but only sensible.
Conclusion
This is a nicely made piece of equipment, but its real-world performance makes it completely unsuitable for its intended purpose. The best you can say is that if you place cold items in it, it’ll keep them cool as long as you keep it supplied with a lot of power. If you don’t use the electric cooler it’ll work almost as well thanks to its insulated construction.
If you are looking for a workable solution to the problem, and insulated box and a block of ice will easily out-perform this arrangement, at far lower purchase and running costs. The low-tech conventional cool-box (Esky) and freezer pack still has a lot going for it. Don’t waste your money on one of these.
Halfords refunded my money very quickly.





